In the face of increasingly sophisticated cyber threats, a layered security approach is paramount. While Content Disarm and Reconstruction (CDR) offers a robust method for sanitizing document-based threats by reconstructing files to eliminate active content, its efficacy is limited when dealing with executable files. Executables, by their nature, cannot be reconstructed without altering their fundamental operation, rendering CDR unsuitable for their sanitization. This limitation necessitates a complementary security mechanism: static code analysis.
Static code analysis, a cornerstone of reverse engineering, provides a critical pre-execution assessment of executable files. By dissecting the code’s structure, logic, and potential behaviors, it unveils hidden threats that might otherwise slip through traditional defenses. This capability is crucial, particularly when CDR’s reconstruction-based approach is inapplicable.
The synergy between CDR and static analysis lies in their distinct, yet complementary, strengths. CDR excels at neutralizing active content within document formats, minimizing the attack surface. Static analysis, conversely, penetrates the opaque nature of executables, revealing potential malicious intent before execution. It’s important to note a crucial distinction: static analysis does not, and cannot, produce definitive “infected/not infected” binary results. Instead, it provides a detailed assessment of the potential threat embodied within the code.
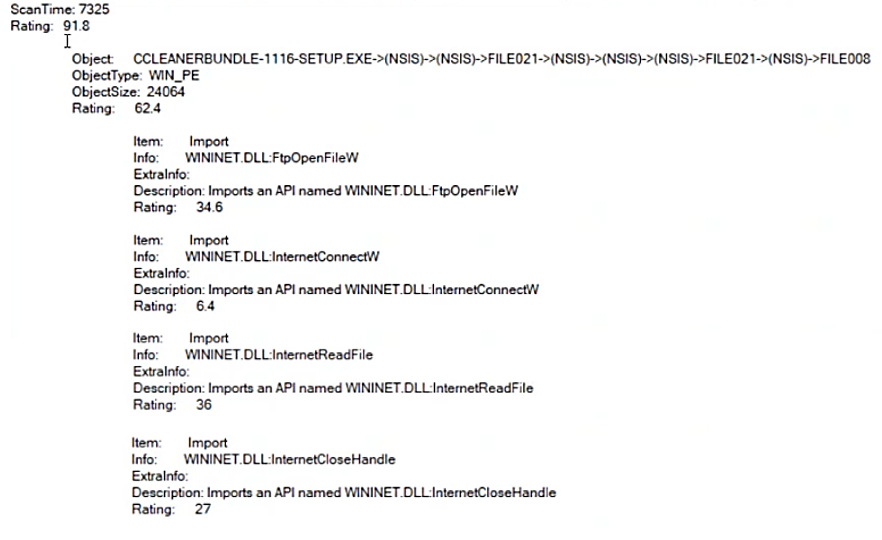
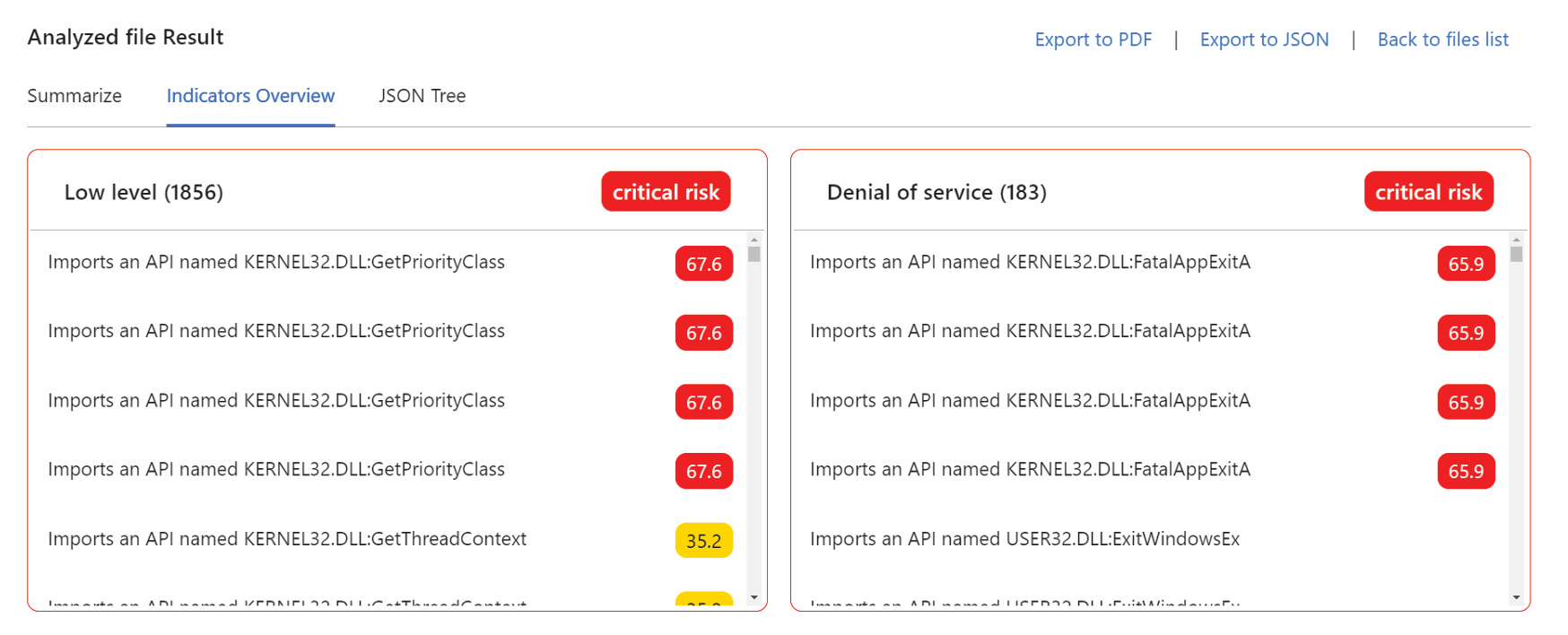
Think of it as a medical diagnostic tool: static analysis reveals risk factors and potential pathologies, but it doesn’t always deliver a conclusive diagnosis of a specific disease. It highlights suspicious API calls, obfuscation techniques, embedded resources, and anomalous code patterns – indicators that warrant further scrutiny. This information empowers security analysts to make informed decisions about the risk associated with a given executable.
For example, static analysis might reveal an executable containing calls to functions associated with file imports, remote code execution or data exfiltration. While this doesn’t definitively label the file as “malware,” it raises a significant red flag, prompting further investigation and potentially triggering quarantine or blocking measures.
This nuanced approach is essential because malware authors constantly evolve their techniques, making signature-based detection less reliable. Static analysis, by focusing on the code’s intrinsic characteristics, provides a more resilient defense against novel and polymorphic threats.
The integration of static code analysis into a comprehensive security architecture, alongside CDR, creates a formidable defense-in-depth strategy. CDR safeguards against document-borne threats, while static analysis provides critical insights into the potential risks posed by executables. This layered approach, combining proactive sanitization with in-depth code analysis, strengthens an organization’s ability to mitigate the ever-present threat of malware and other malicious code. By understanding the limitations of individual security tools and leveraging their complementary strengths, organizations can build a more robust and resilient security posture.