INSIDE TALK – The GateScanner Blog
Blog
Mastering Network Segmentation: A Guide for IT Security Teams
In today’s increasingly complex and fast-changing cyber threat environment, network segmentation is crucial for effective security measures. When implemented correctly, it can significantly reduce the risk of attackers moving laterally within the network, limit the impact of any breaches, and improve overall network performance and manageability. However, achieving effective network segmentation requires a thorough understanding

GS Analyzer: Harnessing Static Binary Analysis to Defend Against Malicious Executables
In cybersecurity, detecting and mitigating threats posed by malicious executable code within benign files is a significant challenge. The 2020 SolarWinds breach exemplifies the damage caused when trusted software updates are compromised, leading to widespread cyber intrusions across government and corporate networks. Malicious executables often remain undetected until activation, as seen in the SolarWinds incident,

Avoiding Data Diode Disasters
Common pitfalls and their mitigations
Data diodes are the go-to solution for securing and segmenting critical networks however, faulty implementation could introduce vulnerabilities. In this post, we’ll explore common pitfalls in data diode implementation – how attackers have taken advantage of them and what you can do to avoid such instances in your network. Configuration Oversights The most obvious and

Strategic Approaches to Minimize Supply Chain Cyber Vulnerabilities
The modern supply chain landscape is a complex web of interconnected entities, spanning across borders and involving intricate digital and physical processes. While these supply chains facilitate global commerce, they also present inherent vulnerabilities and risks, especially in the realm of cybersecurity. In response to these challenges, organizations are increasingly turning to advanced technological strategies

GateScanner Mail Gateway Wins Cybersecurity Award
The winners of the 20th Annual 2024 Globee® Awards for Cybersecurity were announced today with Sasa Software named second in the Email and Web Security category, and first in email security. Sasa Software submitted its innovative GateScanner Mail Gateway solution for the protection of enterprise email, which for the first time offers Content Disarm and

AI-Powered Malware: Preventing the Unknown
Malware developers are leveraging AI algorithms to automate and enhance various stages of the attack lifecycle, from reconnaissance to evasion. This results in stealthier and more targeted attacks that can bypass traditional security measures. Conventional security tools struggle to detect AI-generated malware due to its dynamic and polymorphic nature. As a result, network security teams

Optimizing the Sandbox:
Recognizing and Addressing Limitations
Sandbox technology, a crucial component in cybersecurity, grapples with intricate challenges that necessitate an in-depth understanding for effective mitigation. In this post we will review some approaches to meet current challenges facing this technology. Performance Overhead and Scalability Issues Sandbox environments often face challenges related to performance overhead and scalability. The process of analyzing potential

Safeguarding Medical Imaging Data:
Addressing the Orthanc Osimis DICOM Web Viewer Vulnerability
Healthcare organizations rely heavily on DICOM (Digital Imaging and Communications in Medicine) technology for the storage and exchange of medical imaging data. However, a recent advisory from the Cybersecurity and Infrastructure Security Agency (CISA) has shed light on a critical vulnerability in the Orthanc Osimis DICOM Web Viewer, posing a significant threat to the security of medical imaging data. This

Addressing Security Risks in Digitally Signed PDF Documents
By Yakov Yeroslav, CEO One of the most formidable cyber threats today involves malicious actors exploiting trusted network channels to infiltrate organizations’ infrastructure via infected files – channels that must remain open for regular business operations. To combat this evolving threat landscape, organizations are turning to cutting-edge technology known as Content Disarm & Reconstruction (CDR).

The benefits of a central management
in deployment of multiple “sheep dip” USB anti-malware kiosks
USB drives, while convenient for data storage and transfer, can also introduce several inherent threats to computer systems and networks, such as malware and viruses, autorun exploits and firmware attacks. A commonly used security measure, known by the name “Sheep dip”, is the deployment of USB scanning kiosks. However, to truly maximize the effectiveness of

New study from CISA: CDR reduces risk content in files by >98%
New study from CISA: CDR reduces risk content in files by >98% In a recent study from the Cybersecurity and Infrastructure Security Agency (CISA) that was presented at RSAC 2023 [1], Tom Ruoff and Dr. Olga Livingston showed results of a pilot assessment model for anti-malware controls that tested three CDR solutions in a chained

New threat in RTF files (CVE-202321716)
Critical threat in RTF files (CVE-202321716) Microsoft recently announced a newly discovered vulnerability in RTF files that gives unauthenticated users access to remotely execute commands on host machines. An attacker could send a malicious e-mail containing an RTF payload that would allow execution of commands within the application that was used to open the malicious

Sasa Software Wins Award for Medical Imaging Data Security Solution
Sasa Software Wins Award for Medical Imaging Data Security Solution February 26, 2023, Tel Aviv ‘People and Computers’, the leading Israeli IT portal, has announced its winners for the 2022 ‘Excellence in Computing’ competition, naming Sasa Software as an ‘IT Awards’ winner in the Command & Control category, for the new GateScanner Imaging Gateway that combines
SVG images – the hidden threat your anti-virus can’t see
SVG images – the hidden threat your anti-virus can’t see A new type of file-based attack is spreading quickly, cleverly circumventing standard detection-based protections. This method of attack employes malicious emails with HTML attachments that include embedded, base64-encoded, SVG images. SVG images can, by design, include Javascript tags, and these script tags are now being

DICOM imaging files – a ticking time bomb in healthcare IT security
[Updated January 2023] Recently detected activity of the CLOP ransomware gang involving the compromise and infection of medical imaging CD’s and the DICOM files within, has raised alarm due to the extremely wide exposure represented by this ubiquitous medium.Sasa Software is currently the only cybersecurity vendor offering a dedicated solution for the protection of healthcare networks

Hacking for the Millions: The dark side of ChatGPT
Hacking for the Millions: The dark side of ChatGPT Hacking just got a lot easier. With ChatGPT, even novices can craft cutting edge malicious code with the power of an AI knowledge base. ChatGPT, which stands for Chat Generative Pre-trained Transformer, is a chatbot developed by OpenAI. Launched in November 2022, it has been heralded

Blocking the Raspberry Robin USB Worm
Blocking the Raspberry Robin USB Worm The Microsoft Security Threat Intelligence team recently reported the discovery of activity showing that the Raspberry Robin worm is now part of a complex and interconnected malware ecosystem with links to other malware families and alternate infection methods beyond its original USB drive spread. The investigators found that Raspberry

Sasa Software named Top Infosec Innovator for 2022
Sasa Software named winner of ‘Top Infosec Innovator’ for 2022 TEL AVIV, OCTOBER 27, 2022 – SASA SOFTWARE the cybersecurity industry’s leading provider of Content Disarm and Reconstruction (CDR) network security solutions today announced that is has been named a winner in the Top InfoSec Innovator Awards for 2022. Sasa Software competed against many of

Threat Alert / Critical Infrastructure: Avoslocker
| Threat Alert | Critical Infrastructure | AvosLocker AvosLocker is a Ransomware as a Service (RaaS) affiliate-based group targeting critical infrastructure sectors globally, including, but not limited to, the Financial Services, Critical Manufacturing, and Government Facilities sectors. AvosLocker ransomware encrypts files on a victim’s server and renames them with the “.avos” extension. AvosLocker actors then

Gartner: CDR content sanitization scores high in network infrastructure security
Gartner: CDR content sanitization technology scores high in network infrastructure security Content Disarm and Reconstruction (CDR) technology is identified by Gartner as a ‘high benefit’ technology for network infrastructure security as it continues to mature towards mainstream adoption. In the latest edition of Gartner’s Hype Cycle report on network security (July ’21)[1], content sanitization technology

DICOM: The ‘Invisible’ Vulnerability of Healthcare Networks
DICOM: The ‘Invisible’ Vulnerability of Healthcare Networks Attacks on healthcare systems are a growing concern. Healthcare data is a special category of sensitive data, containing extremely sensitive personal information that make it attractive both for institutional blackmailing – in the form of ransomware, and for individual ransom demands as in the case of high-profile individuals.
New kid on the block: Introducing GateScanner Mail Gateway – an interview with Yakov Yeroslav
On the Future of Email Security Introducing GateScanner Mail Gateway An interview with Yakov Yeroslav, CEO of Sasa Software Q: Sasa Software has been at the forefront of file-based cyber-protection for several years now, with the GateScanner USB Kiosk successfully installed in hundreds of locations around the world. What prompted Sasa Software to go ahead

GISEC Dubai – Live events are back!
GISEC Dubai – Live events are back! By Oren T. Dvoskin / Global Marketing Director @ Sasa Software Face to face meetings are back! We just returned from GISEC 2021– the Gulf’s leading Cybersecurity event. It was our first F2F event and our first business travel outside of Israel since #COVID. It truly dawned on me

Supply Chain Attacks and their impact on OT/ICS Cybersecurity
Supply Chain Attacks and their impact on OT/ICS Cybersecurity Solarwinds and other supply chain attacks are the initial attack vector on organizations – the first link in a sequence of steps to achieve control and disruption. How can industrial networks be protected? Described by Microsoft’s President Brad Smith as the world’s largest and

Lessons Learned from the Oldsmar Water Treatment Cyber attack
Lessons learned from the Oldsmar water supply cyberattack Hacked: The water treatment facility in Oldsmar, FL According to a cybersecurity advisory issued jointly last Thursday (2/11) by the FBI, CISA, UEPA and the Multi State ISAC, unidentified cyber actors had obtained unauthorized access to the supervisory control and data acquisition (SCADA) of a U.S. drinking water

GateScanner – Salesforce connector brings data security to the cloud
GateScanner-Salesforce connector brings CDR data security to the cloud Sasa Software has teamed up with Assuta Medical Centers, Israel’s largest private medical services provider, and Deloitte Digital, the world’s leading professional services firm, to develop a Salesforce security software connector that deliver Salesforce content protection in a transparent, SaaS-based modality.GateScanner® Content Disarm and Reconstruction (CDR) Salesforce connector is

Avoiding Adrozek and other browser-modifier malware
Microsoft Security Research Team has recently reported (December 10) that a browser modifier malware they have named Adrozek has been widely observed in recent months. This malware affects multiple browsers, including Chrome, Edge, Firefox and Yandex Browser. The mechanism of attack is modifying browser settings and DLL files to result in injection of unauthorized ads

Emotet Campaign
Emotet Campaign – Guidance to GateScanner Users Emotet, one of the most famous and dangerous Trojans, has lately been spotted as a part of a mass phishing campaign. The campaign consists of an email which includes a Microsoft Office doc that when clicked gives an Office 365 error message, generated by an obfuscated macro script. The
Tackling Qbot and preventing ransomware attacks
Tackling Qbot and preventing Ransomware Attacks The infamous Qbot banking trojan has recently been spotted again, infecting tens of thousands of machines to date, mainly in the USAlso known as Quakbot, QakBot and Pinkslipbot, the Qbot trojan is a highly-maintained malware, with sophisticated evasion and persistence capabilities, and equipped with a worm-like functionality enabling it

Inside the Garmin cyberattack – Anatomy of the WastedLocker ransomware
Cyberattacks can be personal. Last Thursday, July 23rd, Garmin experienced a massive WastedLocker ransomware attack.
Read about what went behind the scenes.

Sasa Software named “Cool Vendor” by Gartner
Sasa Software named “Cool Vendor” by Gartner, in Cyber-Physical Systems (CPS) Security report 2020. Analyst firm Gartner recently published the “Cool Vendors in Cyber-Physical Systems Security” (CPS) [1] naming Sasa Software in the report. This adds to a previous publication, “Market Guide for Operational Technology Security” [2], identifying Sasa Software in the OT Endpoints Security

GDPR stand aside — meet CCPA!
The interactions between CCPA compliance and Security solutions
Effective Jan 2020, CCPA has implications beyond GDPR.
Do your security solutions support the legislation?

Sasa Software Named multiple Winner of 2020 CDM InfoSec Awards
Sasa Software Wins “Content Disarm and Reconstruction (CDR)” AND “OT/ICS Security” awards announced at the 8th Annual CDM InfoSec Awards at #RSAC 2020
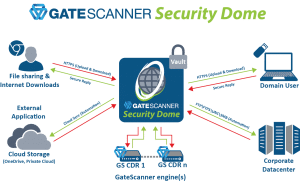
Announcing GateScanner Security Dome: Multi-route Content Disarm and Reconstruction as a Service (CDRaaS)
Launched at #RSAC 2020! GateScanner Security Dome protects multiple content delivery routes, all in one solution,
leveraging GateScanner® CDR to protect against weaponized content that has never been seen before.

Sasa Software Partners with SentinelOne to Offer NextGen AI-driven Security
Sasa Software Partners with SentinelOne to Offer NextGen AI-driven Security First published on SentinelOne blog Content Disarm and Reconstruction (CDR) is designed to provide a safe, hassle-free solution for the prevention of file-based attacks. Instead of relying on signature-based scanning or sandbox behavioral analysis, the technology breaks the file into its components, and then re-creates

Sasa Software has partnered with MedOne to provide global Cloud Services
Together, we are offering GateScanner® Content Disarm and Reconstruction (CDR) solutions as a Service (CDRaaS = CDR as a Service), leveraging MedOne’s Next Generation cloud infrastructures for the highest level of performance, availability, and security.
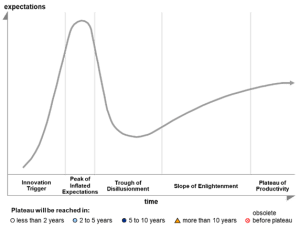
Sasa Software Recognized as a Sample Vendor in the Gartner Hype Cycle for Threat-Facing Technologies, 2019
Gartner, the world’s leading research and advisory company, recently published the Hype Cycle for Threat-Facing Technologies, 2019, identifying Content Disarm and Reconstruction (CDR) on the Peak of Innovation phase of the Hype Cycle.

Portable Media (USB) and NERC CIP Compliance
Industrial systems are under continuous threats- according to a recent study, Half of industrial control system networks have faced cyberattacks in the past year, and removable media (portable media) is identified as the second most common threats to these networks. The cyber threats emanating from USB devices are well documented…
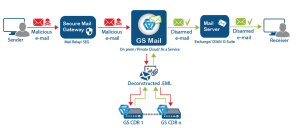
Caution: Can you trust external senders?
The CDR solution will then be able to open the encrypted file and handle its security In recent years, email has been increasingly used by hackers to initiate cyber-attacks. Email Attachments, unsecure links or phishing attacks provide hackers easy access to organizations. According to the Verizon Data Breach Investigation report (DBIR), nearly 50%* of APTs
GateScanner CDR Mail – Password Protected Attachments
In this video we’ll discuss a how GateScanner Mail CDR processes password protected attachments. Adding a password to files encrypts them, creating a challenge to scanning and detection technologies and opening a route of attack. GateScanner Mail CDR solves this with a unique capability for the user to securely provide the password for the file.

Israeli Cyber researchers demonstrate hacking of Siemens Simatic S7 ICS controller
Israeli Cyber researchers demonstrate hacking of Siemens Simatic S7 ICS controller.The vulnerability joins a stream of attacks against infrastructure and utilities, including the “LookBack” State-Nation sponsored malware attack, using a weaponized document to install a remote access Trojan (RAT) to potentially gain control of ICS networks.
GateScanner CDR – Prevention of Stenography attacks
In this session, we review how GateScanner Content Disarm and Reconstruction (CDR) prevents steganography (“stego”) attacks – hiding malware inside of files, and how GS CDR leverages NextGeneration AVs to detect and prevent the attacks.

Sasa APAC in Tech in Gov Canberra, Aug 6-7th ’19
We are excited to announce launching our activities in Australia. Sasa APAC just kicked-off activities at the Tech in Gov conference in Canberra. Want to meet us? Contact us – We’re routinely visiting our Aussie customers and partners.

Sasa Software’s GateScanner successfully blocks ransomware attacks on Assuta Medical Centers
Sasa Software’s GateScanner solution successfully blocks ransomware attacks on Assuta Medical Centers March 1, 2017 Sasa Software’s security solutions, designed for the medical sector, have successfully prevented attacks on the Assuta hospital network. Among other things, sophisticated and unrecognized ransomware attacks were successfully blocked. Assuta – Medical Centers, the largest network of hospitals and medical

Mastering Network Segmentation: A Guide for IT Security Teams
In today’s increasingly complex and fast-changing cyber threat environment, network segmentation is crucial for effective security measures. When implemented correctly, it can significantly reduce the risk of attackers moving laterally within the network, limit the impact of any breaches, and improve overall network performance and manageability. However, achieving effective network segmentation requires a thorough understanding

GS Analyzer: Harnessing Static Binary Analysis to Defend Against Malicious Executables
In cybersecurity, detecting and mitigating threats posed by malicious executable code within benign files is a significant challenge. The 2020 SolarWinds breach exemplifies the damage caused when trusted software updates are compromised, leading to widespread cyber intrusions across government and corporate networks. Malicious executables often remain undetected until activation, as seen in the SolarWinds incident,

Avoiding Data Diode Disasters
Common pitfalls and their mitigations
Data diodes are the go-to solution for securing and segmenting critical networks however, faulty implementation could introduce vulnerabilities. In this post, we’ll explore common pitfalls in data diode implementation – how attackers have taken advantage of them and what you can do to avoid such instances in your network. Configuration Oversights The most obvious and

Strategic Approaches to Minimize Supply Chain Cyber Vulnerabilities
The modern supply chain landscape is a complex web of interconnected entities, spanning across borders and involving intricate digital and physical processes. While these supply chains facilitate global commerce, they also present inherent vulnerabilities and risks, especially in the realm of cybersecurity. In response to these challenges, organizations are increasingly turning to advanced technological strategies

GateScanner Mail Gateway Wins Cybersecurity Award
The winners of the 20th Annual 2024 Globee® Awards for Cybersecurity were announced today with Sasa Software named second in the Email and Web Security category, and first in email security. Sasa Software submitted its innovative GateScanner Mail Gateway solution for the protection of enterprise email, which for the first time offers Content Disarm and

AI-Powered Malware: Preventing the Unknown
Malware developers are leveraging AI algorithms to automate and enhance various stages of the attack lifecycle, from reconnaissance to evasion. This results in stealthier and more targeted attacks that can bypass traditional security measures. Conventional security tools struggle to detect AI-generated malware due to its dynamic and polymorphic nature. As a result, network security teams

Optimizing the Sandbox:
Recognizing and Addressing Limitations
Sandbox technology, a crucial component in cybersecurity, grapples with intricate challenges that necessitate an in-depth understanding for effective mitigation. In this post we will review some approaches to meet current challenges facing this technology. Performance Overhead and Scalability Issues Sandbox environments often face challenges related to performance overhead and scalability. The process of analyzing potential

Safeguarding Medical Imaging Data:
Addressing the Orthanc Osimis DICOM Web Viewer Vulnerability
Healthcare organizations rely heavily on DICOM (Digital Imaging and Communications in Medicine) technology for the storage and exchange of medical imaging data. However, a recent advisory from the Cybersecurity and Infrastructure Security Agency (CISA) has shed light on a critical vulnerability in the Orthanc Osimis DICOM Web Viewer, posing a significant threat to the security of medical imaging data. This

Addressing Security Risks in Digitally Signed PDF Documents
By Yakov Yeroslav, CEO One of the most formidable cyber threats today involves malicious actors exploiting trusted network channels to infiltrate organizations’ infrastructure via infected files – channels that must remain open for regular business operations. To combat this evolving threat landscape, organizations are turning to cutting-edge technology known as Content Disarm & Reconstruction (CDR).

The benefits of a central management
in deployment of multiple “sheep dip” USB anti-malware kiosks
USB drives, while convenient for data storage and transfer, can also introduce several inherent threats to computer systems and networks, such as malware and viruses, autorun exploits and firmware attacks. A commonly used security measure, known by the name “Sheep dip”, is the deployment of USB scanning kiosks. However, to truly maximize the effectiveness of

New study from CISA: CDR reduces risk content in files by >98%
New study from CISA: CDR reduces risk content in files by >98% In a recent study from the Cybersecurity and Infrastructure Security Agency (CISA) that was presented at RSAC 2023 [1], Tom Ruoff and Dr. Olga Livingston showed results of a pilot assessment model for anti-malware controls that tested three CDR solutions in a chained

New threat in RTF files (CVE-202321716)
Critical threat in RTF files (CVE-202321716) Microsoft recently announced a newly discovered vulnerability in RTF files that gives unauthenticated users access to remotely execute commands on host machines. An attacker could send a malicious e-mail containing an RTF payload that would allow execution of commands within the application that was used to open the malicious

Sasa Software Wins Award for Medical Imaging Data Security Solution
Sasa Software Wins Award for Medical Imaging Data Security Solution February 26, 2023, Tel Aviv ‘People and Computers’, the leading Israeli IT portal, has announced its winners for the 2022 ‘Excellence in Computing’ competition, naming Sasa Software as an ‘IT Awards’ winner in the Command & Control category, for the new GateScanner Imaging Gateway that combines

SVG images – the hidden threat your anti-virus can’t see
SVG images – the hidden threat your anti-virus can’t see A new type of file-based attack is spreading quickly, cleverly circumventing standard detection-based protections. This method of attack employes malicious emails with HTML attachments that include embedded, base64-encoded, SVG images. SVG images can, by design, include Javascript tags, and these script tags are now being

DICOM imaging files – a ticking time bomb in healthcare IT security
[Updated January 2023] Recently detected activity of the CLOP ransomware gang involving the compromise and infection of medical imaging CD’s and the DICOM files within, has raised alarm due to the extremely wide exposure represented by this ubiquitous medium.Sasa Software is currently the only cybersecurity vendor offering a dedicated solution for the protection of healthcare networks

Hacking for the Millions: The dark side of ChatGPT
Hacking for the Millions: The dark side of ChatGPT Hacking just got a lot easier. With ChatGPT, even novices can craft cutting edge malicious code with the power of an AI knowledge base. ChatGPT, which stands for Chat Generative Pre-trained Transformer, is a chatbot developed by OpenAI. Launched in November 2022, it has been heralded

Blocking the Raspberry Robin USB Worm
Blocking the Raspberry Robin USB Worm The Microsoft Security Threat Intelligence team recently reported the discovery of activity showing that the Raspberry Robin worm is now part of a complex and interconnected malware ecosystem with links to other malware families and alternate infection methods beyond its original USB drive spread. The investigators found that Raspberry

Sasa Software named Top Infosec Innovator for 2022
Sasa Software named winner of ‘Top Infosec Innovator’ for 2022 TEL AVIV, OCTOBER 27, 2022 – SASA SOFTWARE the cybersecurity industry’s leading provider of Content Disarm and Reconstruction (CDR) network security solutions today announced that is has been named a winner in the Top InfoSec Innovator Awards for 2022. Sasa Software competed against many of

Threat Alert / Critical Infrastructure: Avoslocker
| Threat Alert | Critical Infrastructure | AvosLocker AvosLocker is a Ransomware as a Service (RaaS) affiliate-based group targeting critical infrastructure sectors globally, including, but not limited to, the Financial Services, Critical Manufacturing, and Government Facilities sectors. AvosLocker ransomware encrypts files on a victim’s server and renames them with the “.avos” extension. AvosLocker actors then

Gartner: CDR content sanitization scores high in network infrastructure security
Gartner: CDR content sanitization technology scores high in network infrastructure security Content Disarm and Reconstruction (CDR) technology is identified by Gartner as a ‘high benefit’ technology for network infrastructure security as it continues to mature towards mainstream adoption. In the latest edition of Gartner’s Hype Cycle report on network security (July ’21)[1], content sanitization technology

DICOM: The ‘Invisible’ Vulnerability of Healthcare Networks
DICOM: The ‘Invisible’ Vulnerability of Healthcare Networks Attacks on healthcare systems are a growing concern. Healthcare data is a special category of sensitive data, containing extremely sensitive personal information that make it attractive both for institutional blackmailing – in the form of ransomware, and for individual ransom demands as in the case of high-profile individuals.
New kid on the block: Introducing GateScanner Mail Gateway – an interview with Yakov Yeroslav
On the Future of Email Security Introducing GateScanner Mail Gateway An interview with Yakov Yeroslav, CEO of Sasa Software Q: Sasa Software has been at the forefront of file-based cyber-protection for several years now, with the GateScanner USB Kiosk successfully installed in hundreds of locations around the world. What prompted Sasa Software to go ahead

GISEC Dubai – Live events are back!
GISEC Dubai – Live events are back! By Oren T. Dvoskin / Global Marketing Director @ Sasa Software Face to face meetings are back! We just returned from GISEC 2021– the Gulf’s leading Cybersecurity event. It was our first F2F event and our first business travel outside of Israel since #COVID. It truly dawned on me

Supply Chain Attacks and their impact on OT/ICS Cybersecurity
Supply Chain Attacks and their impact on OT/ICS Cybersecurity Solarwinds and other supply chain attacks are the initial attack vector on organizations – the first link in a sequence of steps to achieve control and disruption. How can industrial networks be protected? Described by Microsoft’s President Brad Smith as the world’s largest and

Lessons Learned from the Oldsmar Water Treatment Cyber attack
Lessons learned from the Oldsmar water supply cyberattack Hacked: The water treatment facility in Oldsmar, FL According to a cybersecurity advisory issued jointly last Thursday (2/11) by the FBI, CISA, UEPA and the Multi State ISAC, unidentified cyber actors had obtained unauthorized access to the supervisory control and data acquisition (SCADA) of a U.S. drinking water

GateScanner – Salesforce connector brings data security to the cloud
GateScanner-Salesforce connector brings CDR data security to the cloud Sasa Software has teamed up with Assuta Medical Centers, Israel’s largest private medical services provider, and Deloitte Digital, the world’s leading professional services firm, to develop a Salesforce security software connector that deliver Salesforce content protection in a transparent, SaaS-based modality.GateScanner® Content Disarm and Reconstruction (CDR) Salesforce connector is

Avoiding Adrozek and other browser-modifier malware
Microsoft Security Research Team has recently reported (December 10) that a browser modifier malware they have named Adrozek has been widely observed in recent months. This malware affects multiple browsers, including Chrome, Edge, Firefox and Yandex Browser. The mechanism of attack is modifying browser settings and DLL files to result in injection of unauthorized ads

Emotet Campaign
Emotet Campaign – Guidance to GateScanner Users Emotet, one of the most famous and dangerous Trojans, has lately been spotted as a part of a mass phishing campaign. The campaign consists of an email which includes a Microsoft Office doc that when clicked gives an Office 365 error message, generated by an obfuscated macro script. The

Tackling Qbot and preventing ransomware attacks
Tackling Qbot and preventing Ransomware Attacks The infamous Qbot banking trojan has recently been spotted again, infecting tens of thousands of machines to date, mainly in the USAlso known as Quakbot, QakBot and Pinkslipbot, the Qbot trojan is a highly-maintained malware, with sophisticated evasion and persistence capabilities, and equipped with a worm-like functionality enabling it

Inside the Garmin cyberattack – Anatomy of the WastedLocker ransomware
Cyberattacks can be personal. Last Thursday, July 23rd, Garmin experienced a massive WastedLocker ransomware attack.
Read about what went behind the scenes.

Sasa Software named “Cool Vendor” by Gartner
Sasa Software named “Cool Vendor” by Gartner, in Cyber-Physical Systems (CPS) Security report 2020. Analyst firm Gartner recently published the “Cool Vendors in Cyber-Physical Systems Security” (CPS) [1] naming Sasa Software in the report. This adds to a previous publication, “Market Guide for Operational Technology Security” [2], identifying Sasa Software in the OT Endpoints Security

GDPR stand aside — meet CCPA!
The interactions between CCPA compliance and Security solutions
Effective Jan 2020, CCPA has implications beyond GDPR.
Do your security solutions support the legislation?

Sasa Software Named multiple Winner of 2020 CDM InfoSec Awards
Sasa Software Wins “Content Disarm and Reconstruction (CDR)” AND “OT/ICS Security” awards announced at the 8th Annual CDM InfoSec Awards at #RSAC 2020

Announcing GateScanner Security Dome: Multi-route Content Disarm and Reconstruction as a Service (CDRaaS)
Launched at #RSAC 2020! GateScanner Security Dome protects multiple content delivery routes, all in one solution,
leveraging GateScanner® CDR to protect against weaponized content that has never been seen before.

Sasa Software Partners with SentinelOne to Offer NextGen AI-driven Security
Sasa Software Partners with SentinelOne to Offer NextGen AI-driven Security First published on SentinelOne blog Content Disarm and Reconstruction (CDR) is designed to provide a safe, hassle-free solution for the prevention of file-based attacks. Instead of relying on signature-based scanning or sandbox behavioral analysis, the technology breaks the file into its components, and then re-creates

Sasa Software has partnered with MedOne to provide global Cloud Services
Together, we are offering GateScanner® Content Disarm and Reconstruction (CDR) solutions as a Service (CDRaaS = CDR as a Service), leveraging MedOne’s Next Generation cloud infrastructures for the highest level of performance, availability, and security.

Sasa Software Recognized as a Sample Vendor in the Gartner Hype Cycle for Threat-Facing Technologies, 2019
Gartner, the world’s leading research and advisory company, recently published the Hype Cycle for Threat-Facing Technologies, 2019, identifying Content Disarm and Reconstruction (CDR) on the Peak of Innovation phase of the Hype Cycle.

Portable Media (USB) and NERC CIP Compliance
Industrial systems are under continuous threats- according to a recent study, Half of industrial control system networks have faced cyberattacks in the past year, and removable media (portable media) is identified as the second most common threats to these networks. The cyber threats emanating from USB devices are well documented…

Caution: Can you trust external senders?
The CDR solution will then be able to open the encrypted file and handle its security In recent years, email has been increasingly used by hackers to initiate cyber-attacks. Email Attachments, unsecure links or phishing attacks provide hackers easy access to organizations. According to the Verizon Data Breach Investigation report (DBIR), nearly 50%* of APTs

GateScanner CDR Mail – Password Protected Attachments
In this video we’ll discuss a how GateScanner Mail CDR processes password protected attachments. Adding a password to files encrypts them, creating a challenge to scanning and detection technologies and opening a route of attack. GateScanner Mail CDR solves this with a unique capability for the user to securely provide the password for the file.

Israeli Cyber researchers demonstrate hacking of Siemens Simatic S7 ICS controller
Israeli Cyber researchers demonstrate hacking of Siemens Simatic S7 ICS controller.The vulnerability joins a stream of attacks against infrastructure and utilities, including the “LookBack” State-Nation sponsored malware attack, using a weaponized document to install a remote access Trojan (RAT) to potentially gain control of ICS networks.

GateScanner CDR – Prevention of Stenography attacks
In this session, we review how GateScanner Content Disarm and Reconstruction (CDR) prevents steganography (“stego”) attacks – hiding malware inside of files, and how GS CDR leverages NextGeneration AVs to detect and prevent the attacks.

Sasa APAC in Tech in Gov Canberra, Aug 6-7th ’19
We are excited to announce launching our activities in Australia. Sasa APAC just kicked-off activities at the Tech in Gov conference in Canberra. Want to meet us? Contact us – We’re routinely visiting our Aussie customers and partners.

Sasa Software’s GateScanner successfully blocks ransomware attacks on Assuta Medical Centers
Sasa Software’s GateScanner solution successfully blocks ransomware attacks on Assuta Medical Centers March 1, 2017 Sasa Software’s security solutions, designed for the medical sector, have successfully prevented attacks on the Assuta hospital network. Among other things, sophisticated and unrecognized ransomware attacks were successfully blocked. Assuta – Medical Centers, the largest network of hospitals and medical

