
Data diodes are the go-to solution for securing and segmenting critical networks however, faulty implementation could introduce vulnerabilities.
In this post, we’ll explore common pitfalls in data diode implementation – how attackers have taken advantage of them and what you can do to avoid such instances in your network.
Configuration Oversights
The most obvious and most common culprit – human error. Improperly configured data diode settings can inadvertently create loopholes for attackers to exploit. This includes misconfigured access controls, or failing to update firmware and software patches regularly.
In 2017 the United States National Security Agency (NSA) was breached by the hacking group Shadow Brokers. The attack is believed to have occurred due to misconfigured access controls on NSA’s data diodes. The attackers exploited vulnerabilities in the configuration, allowing them to exfiltrate classified information.
Effective mitigation calls for for regular audits of the data diode configurations and in addition, strict change management protocols put in place, to control and monitor any modifications that are made to the diode configurations.
Insufficient Monitoring and Logging
Without comprehensive monitoring and logging mechanisms in place, it becomes challenging to detect and respond to suspicious activities or attempted breaches. In 2013, Target suffered a massive data breach where attackers gained access to their network through a third-party HVAC vendor. Target had a data diode in place, but lacked sufficient monitoring capabilities. The breach went undetected for weeks, resulting in the theft of millions of customer records.
Implementing a robust logging mechanism to capture all data transfer activities traveling through the data diode can give security teams critical realtime visibilty into the operation.
Inadequate Physical Security
Attackers can gain access to data diodes physically and tamper with the hardware or connections to manipulate the data flow – or alternately, bypass the diode by gaining physical access to the air-gapped network and insert a malicious USB stick.
In 2016 an undisclosed US government agency experienced a breach when an insider placed a rogue device between the data diode connections, allowing bidirectional data transfer. The Stuxnet worm, discovered in 2010, targeted Iran’s nuclear facilities by exploiting vulnerabilities in the physical security of facilities that resulted in an infected USB stick being inserted into an endpoint inside the isolated environment.
Elevated physical security must be enforced around data diodes and air-gapped networks, with restricted access, tamper-evident seals, and regular inspections to prevent unauthorized modifications.
Incorporating extreme data sanitization technologies such as CDR – at all entry and exit points of the diodes and the provision of safe USB import stations, together ensure that only secure data is flowing into the isolated environment. A pre-requisite would be that a complete disabling of all USB ports inside the air-gapped network, preferably hardware-based, is strictly enforced.
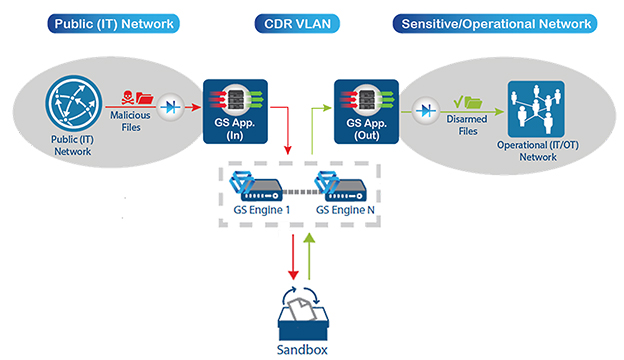
GateScanner CDR processing engines with, sandbox integration,
placed between two GS Injector data diodes,
on route to the air-gapped OT network.
Lack of Redundancy and Failover Mechanisms
Relying solely on a single data diode without redundancy or failover mechanisms increases the risk of disruptions in data flow and potential points of failure.
Best practice involves implementing redundant data diode configurations with automatic failover mechanisms that ensure uninterrupted data flow, in the event of a hardware failure or during maintenance activities.
Inadequate User Training and Awareness
Neglecting to provide adequate training and awareness programs to users leaves them vulnerable to social engineering tactics and unintentional security breaches.
Conducting regular cybersecurity training sessions for employees to educate them on best practices for identifying and mitigating potential security threats. Emphasize the importance of adhering to security policies and procedures especially when interacting with data diode systems that are, in effect, the last barrier against infiltration in many cases.
In conclusion, while data diodes offer an effective means of securing critical networks, their efficacy hinges on proper implementation and maintenance. By addressing common pitfalls and implementing recommended mitigations, organizations can fortify their cybersecurity defenses and mitigate the risk of data breaches and cyber attacks. Stay vigilant, stay secure!
Sasa Software develops CDR solutions to protect networks from file-borne attacks. The GateScanner line offers enhanced CDR protection on a broad range of channels including email, MFT, USB, Web download and medical imaging data transfer
GateScanner Injector package includes a 19″ rack-mounted optical diode (hardware) coupled with dedicated GateScanner Injector software, providing transfer control and automation, complete logging and native interfacing with GateScanner CDR file sanitization engines.

