Blocking the Raspberry Robin USB Worm
The Microsoft Security Threat Intelligence team recently reported the discovery of activity showing that the Raspberry Robin worm is now part of a complex and interconnected malware ecosystem with links to other malware families and alternate infection methods beyond its original USB drive spread.
The investigators found that Raspberry Robin infections lead to follow-on hands-on-keyboard attacks and human-operated ransomware activity, with a very active operation – nearly 3,000 devices in almost 1,000 organizations saw at least one Raspberry Robin payload-related alert in the last 30 days.
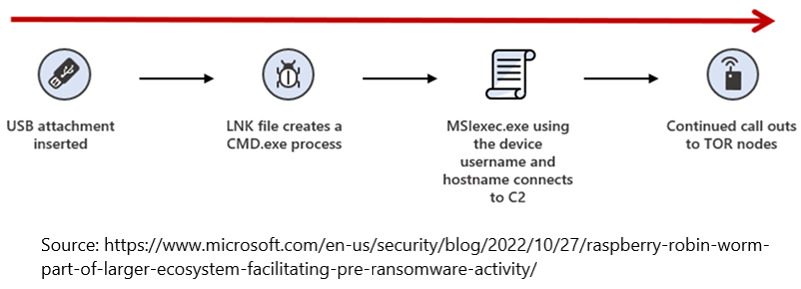
Raspberry Robin’s infection chain is a complex map of multiple infection points that leading to many different outcomes, even in scenarios where two hosts are infected simultaneously. Microsoft found four confirmed entry vectors and they all led to intrusions where the end goal was likely deployment of ransomware.
Mechanism of infection – upon insertion of the infected drive or launching of the LNK file within, the UserAssist registry key in Windows is updated with a new value indicating a program was launched by Windows.
Recommended mitigations include implementation of USB use restrictions through group policies, registry settings and attack surface reduction rules. Needless to say these measures amount to significant limitation on the usefulness of USB for routine file transfer tasks in the enterprise.
An alternative approach – one the enables the continued use of USB in the enterprise, without exposure to cyber threats – would be to implement Content Disarm and Reconstruction (CDR) solutions on endpoints, or to place dedicated USB import stations (Kiosks) in key locations in the enterprise.
GateScanner Desktop and GateScanner Kiosk are two such solutions, providing shielded environments into which users safely insert their devices without endangering network security. GateScanner’s deep scanning capabilities neutralize all malware embedded in the inserted drives – both visible as well as hidden files – preventing the accidental activation or autorun of malware occurring from the source.
Keywords: USB shutdown, USB security, USB vulnerability, Raspbery Robin, USB Worm, Portable media vulnerability, LNK vulnerability, LNK worm,


