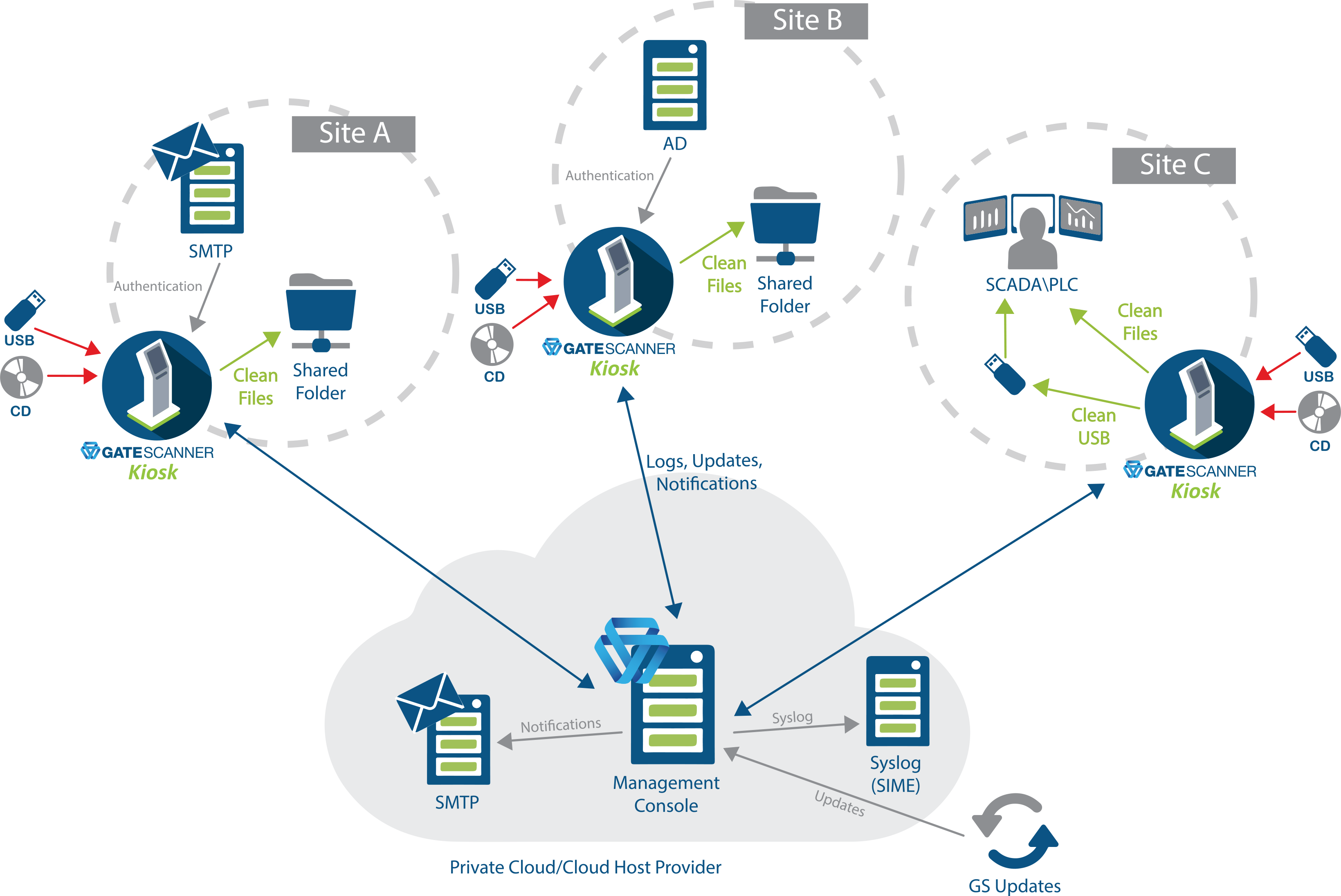
Removable media devices represent a significant attack vector for organizations. USB drives, external hard drives, and other removable media can introduce malware, facilitate data exfiltration, or compromise network integrity if not properly secured. The National Institute of Standards and Technology (NIST) Special Publication 800-53 Revision 5 addresses these concerns through various media protection controls, notably MP-7 (Media Use) and MP-8 (Media Downgrading). This blog explores how removable media malware scanning kiosks provide a meaningful response to these controls while supporting broader media protection objectives.
The Challenge of Removable Media Security
Let’s face it – organizations are caught in a tough spot. They need to allow legitimate use of removable media for business operations while mitigating the inherent risks. Traditional approaches rely heavily on policy enforcement and user training, but these methods alone often prove insufficient. This is where removable media scanning kiosks enter the picture, offering a technological solution that complements administrative controls.
Understanding NIST SP 800-53r5 Media Protection Controls
Before examining how scanning kiosks address specific requirements, let’s review the key media protection controls relevant to our discussion:
MP-7: Media Use
This control focuses on restricting or prohibiting the use of organization-defined types of media on systems or system components using organization-defined security safeguards. The primary objectives are to:
- Establish usage restrictions and implementation guidance for controlled media
- Prohibit the use of removable storage devices when necessary
- Limit media types to those with identifiable owners
MP-8: Media Downgrading
This control addresses the process of reducing the security categorization level of media containing sensitive information. Key aspects include:
- Implementing a verifiable downgrading process
- Ensuring media sanitization techniques are commensurate with security categorization
- Tracking, documenting, and verifying media downgrading actions
How Removable Media Scanning Kiosks Address MP-7 Requirements
Removable media scanning kiosks serve as a technological implementation of MP-7 by providing:
1. Controlled Access Point for Media Inspection
Rather than simply relying on policy to restrict media use, kiosks establish a physical checkpoint where all removable media must be scanned before connection to organizational systems. This directly implements the “organization-defined security safeguards” mentioned in MP-7.
2. Media Type Verification and Restriction
Advanced scanning kiosks can identify media types, allowing organizations to enforce policies that restrict the use of certain media formats. If an organization prohibits the use of specific devices (e.g., certain brands or types of USB drives), the kiosk can enforce this restriction.
3. User Attribution and Accountability
Many kiosks incorporate user authentication mechanisms, ensuring that media use can be tracked to specific individuals. This addresses the MP-7 requirement for media to have identifiable owners. The kiosk logs can provide an audit trail of who scanned what media and when.
4. Malware Detection and Isolation
By scanning media in an isolated environment before it connects to organizational systems, kiosks provide a critical security safeguard against malware introduction. This functionality directly supports MP-7’s objective of preventing unauthorized or malicious code from entering the network via removable media.
Addressing MP-8 Requirements Through Scanning Kiosks
While MP-8 primarily focuses on downgrading media security categorization, scanning kiosks can support this process in several ways:
1. Verification of Sanitization Status
Kiosks equipped with appropriate tools can verify whether media has been properly sanitized as part of the downgrading process. This provides the verification mechanism required by MP-8.
2. Documentation and Tracking
Advanced kiosks can maintain logs of media scanning activities, providing documentation of downgrading processes. These logs can be integrated with organizational tracking systems to fulfill the documentation requirements of MP-8.
3. Security Categorization Assessment
Some scanning kiosks can analyze media content to determine the presence of sensitive information, assisting in the security categorization process that underpins media downgrading decisions.
4. Data Loss Prevention for Downgrading Support
Many modern anti-malware kiosks include Data Loss Prevention (DLP) capabilities that directly support the media downgrading requirements of MP-8. These DLP features scan for sensitive content such as personally identifiable information (PII), intellectual property, classified documents, or other controlled unclassified information. By identifying and flagging such content, the kiosk becomes a useful tool in the downgrading process by:
- Automating identification of sensitive data requiring special handling
- Providing options for content redaction or removal to facilitate downgrading
- Enforcing consistent application of downgrading standards
- Creating verifiable evidence that media has been appropriately cleared of higher-level content
This dual-purpose functionality makes kiosks particularly valuable in environments where media regularly moves between different security domains or classification levels.
Central Management of Networked Kiosks: Enhancing NIST Compliance
The implementation of centrally managed, networked anti-malware kiosks provides significant advantages in meeting NIST requirements across multiple control families:
1. Consistent Policy Enforcement (MP-7)
A central management system ensures uniform application of media use policies across all entry points. This consistency is critical for MP-7 compliance, eliminating potential security gaps that might arise from disparate configuration of individual kiosks.
2. Comprehensive Auditing and Monitoring (AU-2, AU-6)
Centralized logging and monitoring of all kiosk activities supports NIST audit requirements by:
- Aggregating scan data from all locations to identify organization-wide trends
- Enabling real-time alerting of suspicious activities across the kiosk network
- Providing centralized reporting capabilities for compliance verification
3. Configuration Management Support (CM-2, CM-6)
Centrally managed kiosks facilitate compliance with configuration management controls by:
- Enabling automated deployment of security baseline updates to all kiosks
- Ensuring all devices maintain identical security configurations
- Allowing rapid response to newly identified threats through centralized updates
4. Incident Response Coordination (IR-4)
When malware or policy violations are detected, centrally managed kiosks support incident response by:
- Immediately sharing threat intelligence across all checkpoints
- Enabling coordinated containment actions organization-wide
- Providing centralized forensic data collection for incident analysis
This enterprise-level visibility and control transforms individual security checkpoints into a cohesive security boundary, significantly enhancing the organization’s ability to meet various NIST control requirements while improving operational efficiency.
Beyond MP-7 and MP-8: Additional NIST Controls Addressed
Removable media scanning kiosks don’t just address MP-7 and MP-8; they provide meaningful support for several other media protection and system protection controls:
MP-2: Media Access
Kiosks restrict access to information system media to authorized users, providing a technical enforcement mechanism for media access policies.
MP-4: Media Storage
By scanning media before it enters secure storage areas, kiosks help ensure that stored media meets organizational security requirements.
MP-6: Media Sanitization
Advanced kiosks can verify sanitization effectiveness, supporting the verification requirements of MP-6.
SI-3: Malicious Code Protection
Kiosks directly implement malicious code protection for a key attack vector, complementing endpoint protection solutions.
SI-7: Software, Firmware, and Information Integrity
By scanning for tampered files or unauthorized content, kiosks help verify the integrity of information stored on removable media.
Key Features of Effective Removable Media Scanning Kiosks
To provide comprehensive support for NIST media protection controls, scanning kiosks should include:
- Multiple Scanning Engines: Utilizing multiple anti-malware engines to maximize detection rates
- Isolated Environment: Operating in an air-gapped or controlled network segment to prevent malware escape
- File Type Analysis: Identifying and restricting unauthorized file types
- Media Type Control: Recognizing and enforcing policies for different media formats
- Comprehensive Logging: Maintaining detailed audit trails of all scanning activities
- User Authentication: Requiring user identification for accountability
- Content Verification: Checking for sensitive data that might violate organizational policies
- DLP Capabilities: Scanning for and managing sensitive organizational data
Implementation Considerations for Maximum Effectiveness
Organizations deploying removable media scanning kiosks should consider the following factors to maximize their effectiveness in addressing NIST controls:
- Strategic Placement: Locate kiosks at physical entry points to secure areas or at network boundary points
- Integration with Existing Processes: Align kiosk use with broader security workflows and incident response procedures
- Regular Updates: Maintain current malware signatures and scanning engines
- User Training: Educate staff on proper kiosk use and the importance of the scanning process
- Policy Alignment: Ensure media use policies explicitly incorporate kiosk scanning requirements
- Centralized Management: Implement enterprise management for consistent policy enforcement and comprehensive monitoring
To sum it all up, removable media malware scanning kiosks provide a practical, technological response to the media protection challenges addressed in NIST SP 800-53r5. By implementing these solutions as part of a comprehensive media protection strategy, organizations can significantly reduce risks associated with removable media while demonstrating compliance with multiple NIST controls.
These kiosks bridge the gap between policy and practice, transforming abstract requirements into concrete security measures. The integration of DLP capabilities further enhances their value by supporting media downgrading processes, while centralized management ensures consistent security posture across the enterprise. In today’s evolving threat landscape, the combination of clear policies, user awareness, and technological safeguards like scanning kiosks represents the most effective approach to media protection.
For organizations subject to NIST compliance requirements, removable media scanning kiosks aren’t just a convenience—they’re an essential component of a robust security architecture that addresses multiple control families simultaneously.