In recent years, email has been increasingly used by hackers to initiate cyber-attacks. Email Attachments, unsecure links or phishing attacks provide hackers easy access to organizations. According to the Verizon Data Breach Investigation report (DBIR), nearly 50%* of APTs that have caused significant damage to organizations have come through emails. And this trend is increasing every year.
It is important to remember that it is not only email attachments that can contain a threat. According to RFC 5322, the email body can contain over 200 embedded elements.
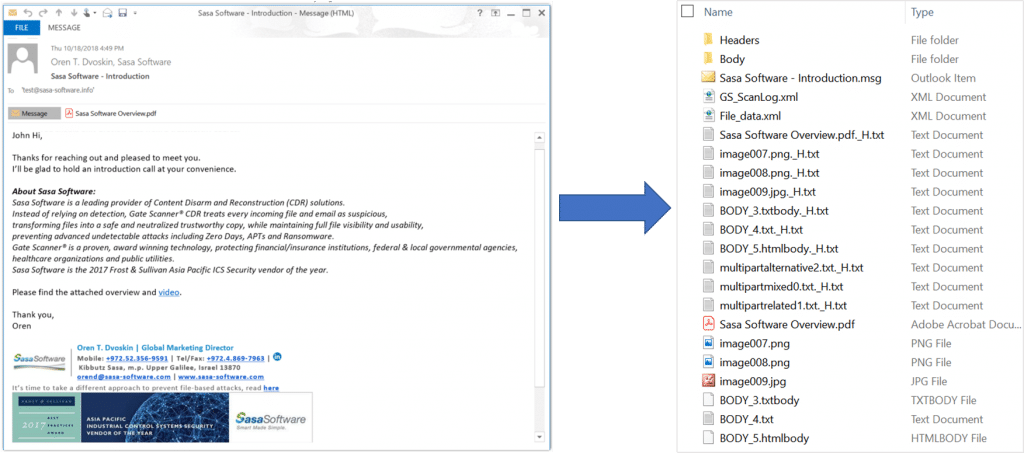
One message, multiple attack vectors. An email as deconstructed by GateScanner® Mail
This means we must treat the e-mail body itself as an attachment. Hackers are increasingly using this method to engage in server attacks against a specific client.
Unfortunately, even the best email gateway from the best vendors fail to treat and to detect these sophisticated attacks. Even if they do eventually, it is too late, causing significant financial losses to the organization.
Email gateway vendors are aware that email is a difficult channel to protect and there are significant challenges for the existing technologies to cope with new and unknown attacks. As such, we are seeing a new phenomenon -Each external email received (and scanned by the email gateway) is presented with the following prompt to the receiver:
CAUTION: External Sender, Do not click on links or open attachments unless you recognize the sender.
Employee awareness is indeed a very important issue, but how effective is the warning message in preventing attacks?
First, the hackers often know to spoof the source of the email in a way that makes the employee think that the email came from a legitimate/ trusted source.
Second, even when receiving an email from a reliable and recognized source, how can we identify whether the sender’s network, computer, or email is not infected?
The truth is, we can’t! Therefore, a warning message attached to the email is almost meaningless. Rather than protecting the receiver, it indicates the weakness of the organization’s security solution.
So, what can be done do mitigate this weakness? This is where Content Disarm and reconstruction (CDR) technology comes in. Every self-respecting CDR vendor has a whole host of detection and diagnosis tools. Nevertheless, even when the detection and diagnosis didn’t find a threat in the file; it still remains “suspicious” as it might contain unfound embedded threats. These threats will then enter the organization’s network via email and can be activated immediately or at a later date. This is where the proprietary reconstruction capabilities of GateScanner® CDR plays a vital role. The reconstruction technology changes the structure of the file in order to neutralize any undetected embedded threat.
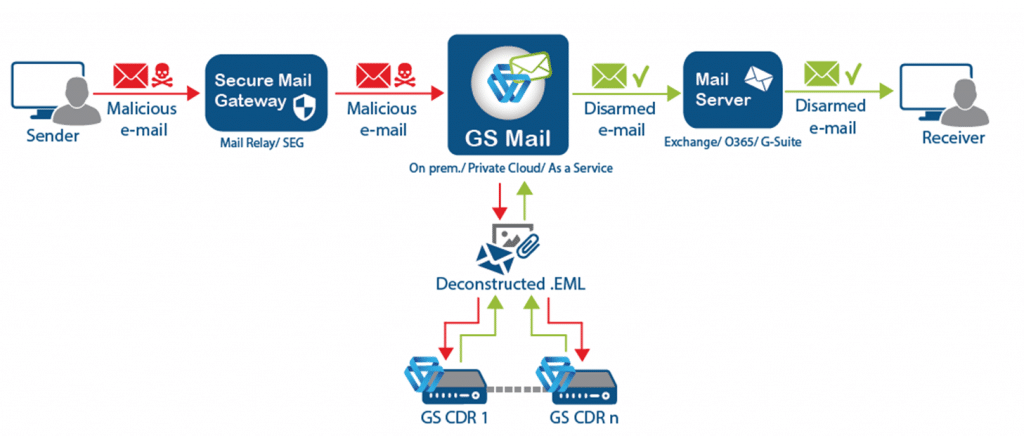
Given that the email body must be considered a threat, and as such, treated in the same manner as an attachment, our CDR solution is ideal. It is capable of dismantling and reconstructing both the attachment and the email body, reassembling the email, and forwarding it on to its destination.
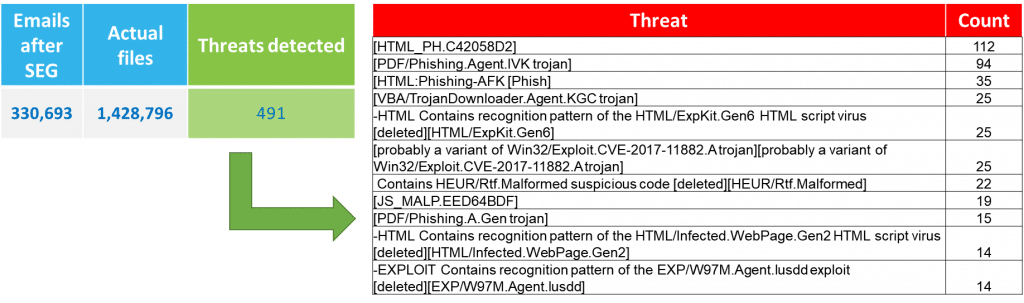
Additionally, there is the problem of receiving emails with encrypted/password protected attachments. For example, an employee who receives their monthly pay stub as an encrypted PDF. What is the organization’s policy in this case? Do they block the email even though the employee needs this document? Allowing the employee to receive the email means, it enters the organization’s network. This will then bypass most of the organization’s network protection systems and will present as a serious risk to the organization. Any reputable CDR solution must block and quarantine encrypted emails, blocking it temporarily from entering the organization until the user provides a password. The CDR solution will then be able to open the encrypted file and handle its security with the same precision as of the non-encrypted emails.
Reconstruction has proven itself time and time again. Only recently, Gartner published its recommendation to add CDR as a high priority, best practice, in the line of technologies used for email protection. The researched highlighted the deficiencies of signature based solutions, weaknesses of sandboxing and noting that, “CDR protects against exploits and weaponized content that have not been seen before”. Gartner also predicted a significant increase in the adoption of CDR technology over the coming years.


