NERC CIP Portable Media Security Compliance for OT & ICS

Industrial systems are under continuous threat- according to a recent study, half of industrial control system networks have faced cyberattacks in the past year, and removable media (portable media) is identified as the second most common threats to these networks.
The cyber threats emanating from USB devices are well documented with researchers from the Ben-Gurion University of Israel identifying over 29 ways in which USB devices can be exploited to compromise target computers.
The research illustrates the multiple dangers of using USB devices, as they can contain not only malicious files, but the media itself can be used to attack the target network using compromised firmware, hidden partitions, and even deploying destructive electrical charges.
Famously, Stuxnet that sabotaged Iran’s Natanz nuclear power station in 2010, demonstrated that USB devices can be used to attack air-gapped networks. Since then, numerous incidents have continually proven that negligent employees and malicious insiders will plug compromised USB devices into networks, potentially causing security incidents. Recently, the US Secret services apprehended a USB device containing malware at President Trump’s Mar-a-Lago resort. Other incidents are well documents. For instance, an employee used a USB drive to download and view a movie on a critical infrastructure computer in the Middle East. This released a piece of malware known as Copperfield that could result in data leakage, remote control of an ICS workstation and network scanning. In another incident, a U.S. service member stationed at a DoD facility in Afghanistan (fall 2008) inserted a thumb drive, which Pentagon officials believe Russian spies infected with malicious code, into a laptop, allowing Russian spies to enter SIPRNet, the Pentagon’s secret internal network. USB devices have also been used to spread crypto-mining malware, in a purely-commercially motivated attack.
These incidents have prompted commercial organizations to self-enforce USB lockdown procedures. Notably, IBM announced banning employees from using the devices. The North American Electric Reliability Corporation (NERC) established CIP-010-2 R4, a standard aimed at preventing unauthorized access or malware propagation to BES (Bulk Electric System) Cyber Systems through Transient Cyber Assets or Removable Media; and (2) Preventing unauthorized access to BES Cyber System Information through Transient Cyber Assets or Removable Media.
This is now being extended to NERC CIP 003-7 which will require operators to protect low impact (or less critical) BES Cyber Systems as well. This new regulatory requirement comes into effect on January 1st of 2020. The regulation serves as strong evidence that utilities and their regulators understand that the concept of “air-gap” is no longer valid; in an interconnected world it is impossible to ensure that any system, no matter how well guarded, will be completely shut-off from the external world. Complying with CIP-003-7 requires to manage access of USB devices and detect unauthorized use of such devices. Utilities should install portable media ‘safe ports’ or Cybersecurity Kiosks in central locations throughout the facility and limit the use of USB devices through these USB scanning kiosks only. Files uploaded through these anti-malware kiosks should be scanned and disarmed by CDR technology to ensure that no malware will gain entrance into internal networks and that networks will be protected from media based attacks
Famously, Stuxnet that sabotaged Iran’s Natanz nuclear power station in 2010, demonstrated that USB devices can be used to attack air-gapped networks. Since then, numerous incidents have continually proven that negligent employees and malicious insiders will plug compromised USB devices into networks, potentially causing security incidents. Recently, the US Secret services apprehended a USB device containing malware at President Trump’s Mar-a-Lago resort. Other incidents are well documents. For instance, an employee used a USB drive to download and view a movie on a critical infrastructure computer in the Middle East. This released a piece of malware known as Copperfield that could result in data leakage, remote control of an ICS workstation and network scanning. In another incident, a U.S. service member stationed at a DoD facility in Afghanistan (fall 2008) inserted a thumb drive, which Pentagon officials believe Russian spies infected with malicious code, into a laptop, allowing Russian spies to enter SIPRNet, the Pentagon’s secret internal network. USB devices have also been used to spread crypto-mining malware, in a purely-commercially motivated attack.
These incidents have prompted commercial organizations to self-enforce USB lockdown procedures. Notably, IBM announced banning employees from using the devices. The North American Electric Reliability Corporation (NERC) established CIP-010-2 R4, a standard aimed at preventing unauthorized access or malware propagation to BES (Bulk Electric System) Cyber Systems through Transient Cyber Assets or Removable Media; and (2) Preventing unauthorized access to BES Cyber System Information through Transient Cyber Assets or Removable Media.
This is now being extended to NERC CIP 003-7 which will require operators to protect low impact (or less critical) BES Cyber Systems as well. This new regulatory requirement comes into effect on January 1st of 2020. The regulation serves as strong evidence that utilities and their regulators understand that the concept of “air-gap” is no longer valid; in an interconnected world it is impossible to ensure that any system, no matter how well guarded, will be completely shut-off from the external world. Complying with CIP-003-7 requires to manage access of USB devices and detect unauthorized use of such devices. Utilities should install portable media ‘safe ports’ or Cybersecurity Kiosks in central locations throughout the facility and limit the use of USB devices through these USB scanning kiosks only. Files uploaded through these anti-malware kiosks should be scanned and disarmed by CDR technology to ensure that no malware will gain entrance into internal networks and that networks will be protected from media based attacks
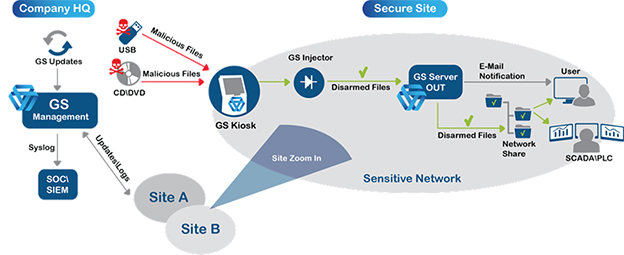
Conceptual Cybersecurity Anti-Malware Kiosk deployment
Centrally managed cyber security kiosks are geographically distributed at multiple sites.
Files are copied from portable media and multi-scanned/disarmed to trusted media or delivered securely into the OT network using a data diode.
Centrally managed cyber security kiosks are geographically distributed at multiple sites.
Files are copied from portable media and multi-scanned/disarmed to trusted media or delivered securely into the OT network using a data diode.
Alternatively, they could use a dedicated Desktop client applications or Web based portal that takes control of computer’s USB ports and submit all uploads to the GateScanner CDR engine for processing to transforms all incoming files into harmless, safe & neutralized copies.

