Content Disarm Reconstruction Cdr: Secure Your Digital Infrastructure
Content Disarm and Reconstruction Technology (CDR)
WHAT IS CONTENT DISARM AND RECONSTRUCTION (CDR) TECHNOLOGY?
Also known as ‘file sanitization’ or ‘content sanitization’ – Content Disarm and Reconstruction (CDR) is an advanced technology providing superior results in the prevention of file-based attacks – effectively blocking the initial access phase of most APT’s, ransomware and zero-day attacks. CDR generates for each incoming email and file, a functionally identical new copy that is devoid of any malicious content or links – transparently, in near real-time.
How DOES CONTENT DISARM AND RECONSTRUCTION (CDR) TECHNOLOGY WORK?
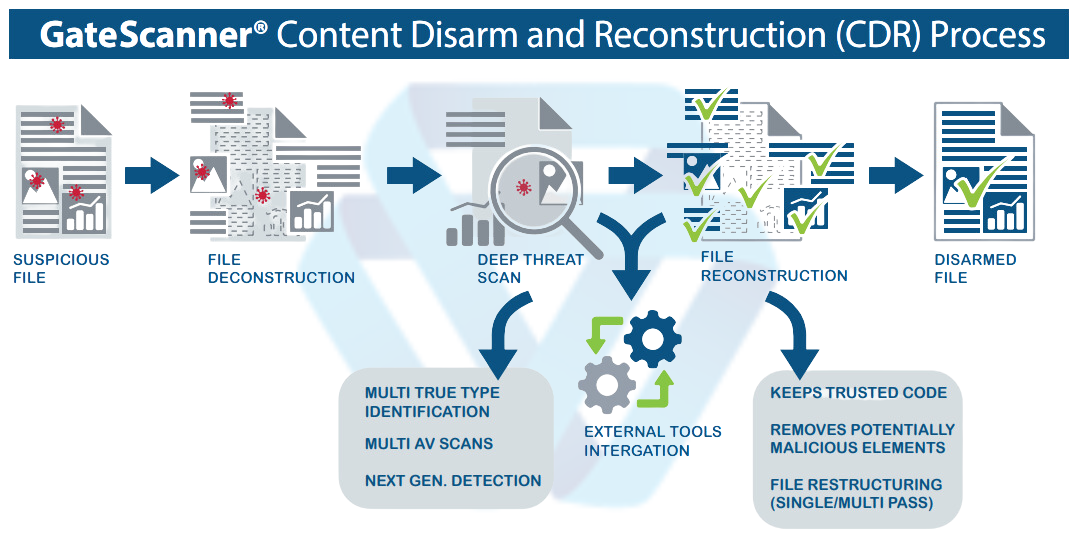
Content Disarm and Reconstruction dissects each incoming (or outgoing) file to its most elementary components and scans the components with NextGen AI and multi-AV tools with superior results. It then reconstitutes the files, in strict adherence to their vendor specifications, disrupting in process any remaining, undetected (‘signature-less’) malware (see our ‘Before & After CDR Processing’ samples page).
A good CDR solution combines deep Deconstruction/Reconstitution processing, coupled with high-throughput capacity.
Content Disarm and Reconstruction stages
- 1. File is deconstructed to its elementary components, and scans and mitigations are applied to each individual component. These include multi file-type verifications, multi-AV scans, static code analysis on binary segments and the optional disabling of active components such as macros and embedded scripts by defined profiles.
- 2. File reconstruction through transformation that removes any remaining unknown and undetected malicious code, foreign to vendor-specified format.
Why GateScanner?
Excellence. We are certain that our CDR technology is practically impregnable. Our clients’ independent penetration tests repeatedly show up to 99.99 % success rates in the obstruction of unknown, file-borne threats, and that’s the bottom line – but that’s not the whole story…
Modularity. Adding a new component to an existing system can be a major challenge, and flexibility is the key to a successful implementation. With this in mind, we’ve built GateScanner to be modular, highly configurable and easily scalable. Pick and choose any part of the CDR process you want to implement, select which channels to protect, and chain up to ten GateScanner engines on-the-fly, to achieve virtually unlimited processing capacity.
Easily Integrated. Challenged to deliver unique solutions for a wide variety of client configurations, GateScanner features a unique integration engine that enables security teams to insert content sanitization processing at any point along the data flow, before or after existing security tools, notching-up the security profile of the network significantly.
Customizable. For us, every client is an opportunity to get creative. Our highly dedicated development team works closely with each client to fulfill their most ambitious goals.
We look forward to creating your solution!
Scalable. GateScanner’s CDR engines are implemented in Active-Active configuration enabling no-downtime scalability, making the addition of more processing power as easy as a click of a button.
Experience. GateScanner is in continuous development since 2013. With a diverse client-base, ranging from government security agencies and defense contractors, through multi-national manufacturing industries and critical infrastructure providers, to financial institutions and national healthcare providers, we consistently deliver our proven technology and maintain our clients’ continuing trust year after year.
GateScanner features:
GateScanner achieves prevention levels of up to 99.99% for undetectable threats, protecting organizations from APT’s, Zero-days, ransomware and other file-based attacks.
CDR deep-scans of deconstructed files with multi antivirus tools, including Next-Gen AI/ML AV, reaching detection levels of up to 2.5 times the rate of detection for the original composite file scan.
Hundreds of file types supported including the entire suite of MS Office, PDF, media files (images, audio, video), AutoCad, Hanword (HWP), Archives, PST, .EML, installation files, XML, HTML, other text files, medical imaging files (DICOM), and customized files. (See “Before & After CDR processing” samples page).
Extreme flexibility – the GateScanner solution is modular, scalable and highly configurable
Built-in external-tools integration upgrades performance of existing security tools
GateScanner implements CDR technology to protect email, portable media uploads, cross-network file transfers, safe browser downloads, Cloud-based file shares, computing appliances and to enable cross domain solutions with unidirectional gateways.
All processing is on the client side. No vendor involvement
Sasa Software is privately owned by Kibbutz Sasa, Israel, with the majority of profits channeled back into R&D.


