File-Based Attacks: Blocked at the Gate
File-based Attacks:
Blocked at the Gate
GateScanner® provides robust protection against file-based threats, ensuring your network stays safe from malicious files and emails.
GateScanner eliminates advanced and unknown malware, delivering clean, secure content on every channel, without delay.
GateScanner® ensures that your network stays safe from file-based threats,
including advanced, highly obfuscated or unknown malware.
Threat-free files and emails delivered seamlessly on any channel, without delay.
GateScanner. Security Beyond Detection
HOW GATESCANNER WORKS
DISARM
RECONSTRUCT
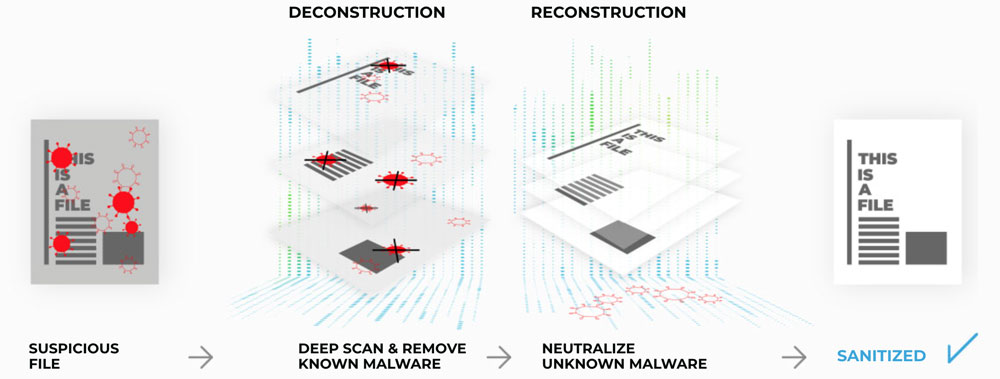
SUSPICIOUS
FILE
DEEP SCAN & REMOVE
KNOWN MALWARE
NEUTRALIZE
UNKNOWN MALWARE
SANITIZED
Content Disarm and Reconstruction (CDR) technology
applies multi-AV scanning and file transformation to neutralize threats at network level
Content Disarm and Reconstruction
applies multi-AV scanning
and file transformation
to neutralize threats
at network level
Trust Your Files
CDR file sanitization
prevention on every channel
Email
Security
Inline
Data Security
Secure
MFT
Secure
Web download
Removable Media
Security
A full-featured Secure Email Gateway or as an SMTP Mail Relay service.
Choose your option for CDR-enhanced email security
CDR file sanitization delivered via REST API/ICAP
Secure file transfer and share with built-in CDR file sanitization
Secure web downloads with a CDR extension for Chromium based browsers (Chrome, Edge and others)
Protect the organization from malicious content arriving on removable media with GateScanner Kiosk and Desktop CDR
CDR file sanitization
prevention on every channel
Email Security
done right
As a full-featured email Gateway or as an SMTP relay – you get fully integrated CDR email security
Secure
Web downloads
Secure browser downloads with CDR download sanitization extension for Chromium-based browsers (Chrome, Edge and others)
Removable Media
Security
Protect the organization from malicious content arriving on removable media with GateScanner Kiosk and Desktop CDR file sanitization solutions
Prevent the Undetectable
WE PROTECT THEM TOO
LONG TERM CLIENTS













































REQUEST A DEMO
Let us show you GateScanner in action
BUILT TO PROTECT
Initially developed to protect a U.S. Army contractor, GateScanner is designed to perform in extremely high-threat environments,
and is the choice of critical networks in government, infrastructure and enterprise around the world.
BUILT TO PROTECT
GateScanner is designed to perform in extremely high-threat environments,
and is the choice of critical networks in government, infrastructure and enterprise around the world.
proven protection







Gartner Disclaimer: The GARTNER COOL VENDOR badge is a trademark and service mark of Gartner, Inc. and/or its affiliates and is used herein with permission. All rights reserved. Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s Research & Advisory organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.



