<span style="mso-ascii-font-family:Calibri;mso-fareast-font-family:"Times New Roman";
Sasa Software named “Cool Vendor” by Gartner, in Cyber-Physical Systems (CPS) Security report 2020.
Analyst firm Gartner recently published the “Cool Vendors in Cyber-Physical Systems Security” (CPS) [1] naming Sasa Software in the report. This adds to a previous publication, “Market Guide for Operational Technology Security” [2], identifying Sasa Software in the OT Endpoints Security category. The Gartner “Cool Vendor” report names companies who “have developed innovative tools and applications that improve security and safety to support the emergence of cyber-physical systems”.
The report mentions that Sasa Software’s solutions can help in scenarios where content, which can be malicious, is introduced by employees or third-party contractors. Use cases described include portable media (USBs), as well as operational appliances such as SCADA controllers.
Sasa Software identifies several risks unique to CPS, Operational Technologies (OT), and Industrial Control System (ICS) security environments:
CPS, OT, and ICS systems are a critical component of the organization, having a unique interaction with the physical world, where security incidents can lead to critical shutdown and damages.
The number of incidents affecting these systems is on the rise with events such as the Norsk Hydro LogerGoga ransomware attack, ASUS incident, Garmin WastedLocker incident, and recent chain of attacks on US Utilities, with the focus switching towards operational disruption rather than financial gains or espionage.
Increase in OT specific Zero-Day and vulnerability disclosures. For example, Siemens disclosed a vulnerability in its S7 PLC, adding to an increasing list of vulnerabilities being published, indicating a growing interest from the security community in researching these vulnerabilities.
Increase in Government Regulations – this is a positive step, but it increases the burden on end-users to adapt security solutions and to exhibit compliance, these include NERC CIP 003-7, NEI 08-09, NIST 800-53, PCI DSS, CCPA, GDPR, and others.
Continued usage of portable media such as USB drives and other transient cyber assets (TCA’s). These pose an acute concern as they can contain both malicious hardware/firmware and file-based attacks. The FBI recently wanted against the usage of USBs containing bad firmware (BadUSB, RubberDucky, BashBunny).
The reliance on CPS/OT and ICS appliances such as SCADA controllers and IoT devices that cannot be installed with traditional cybersecurity solutions so are vulnerable to attacks.
Addressing CPS/OT/ICS security risks requires specialized solutions addressing the unique challenges and requirements in these environments. Sasa Software recommends considering the following use cases:
Ingestion of external files into OT environment: OT security best practices and regulations like NERC CIP 003-7 and NIST 800-53 PR.PT-2 call for scanning of all files and TCA’s (Transient Cyber Assets) and portable (USB) media devices before the introduction to high impact networks. The GateScanner Cyber security Kiosk is the only one that not only sanitizes the files but also ensures that the anti-virus Kiosk itself will not be infected. This reduces the risk that a rogue USB device (like RubberDuckey) could somehow find its way into the OT environment and deliver its malicious payload. For instance, software developed in a lab environment should be transferred by a portable media device to a USB scanniong cyber security kiosk, then the files should be sanitized/ scanned by the CDR technology, and then another whitelisted USB device should be used to transfer these to the production environment/ machinery. CDR could also be used for scanning portable devices and ensuring that their firmware isn’t malicious.

- Introduction of appliances and computing devices into an OT/ICS/SCADA network: OT appliances such as SCADA controllers and PLC typically cannot be directly installed with security solutions due to the usage of legacy operating systems (Win XP, 2000, NT, etc) and since installing additional software can impair the operation of the device or void its manufacturer warranty. This poses a challenge since these appliances can be delivered with malicious firmware or be compromised during ongoing operations or while undergoing maintenance. Another scenario when external contractors arrive with a laptop or other diagnostic equipment that will be connected directly to the target network. GateScanner Appliance Security solves this scenario by running a Mult-AV full-HDD scan on the appliance in memory, without installing software and without making configuration changes.
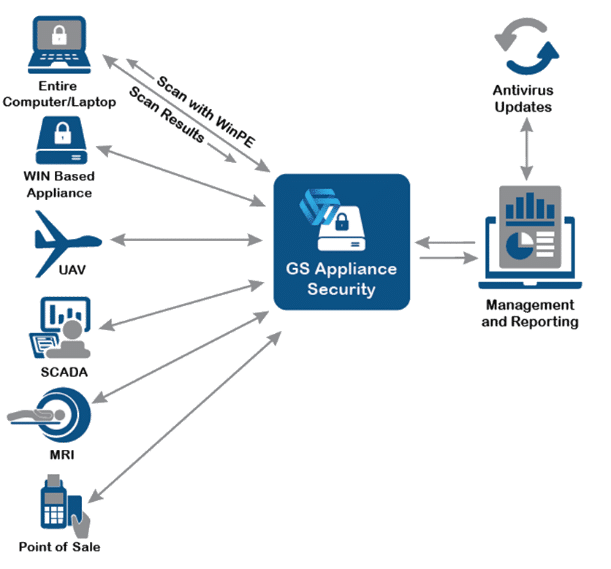
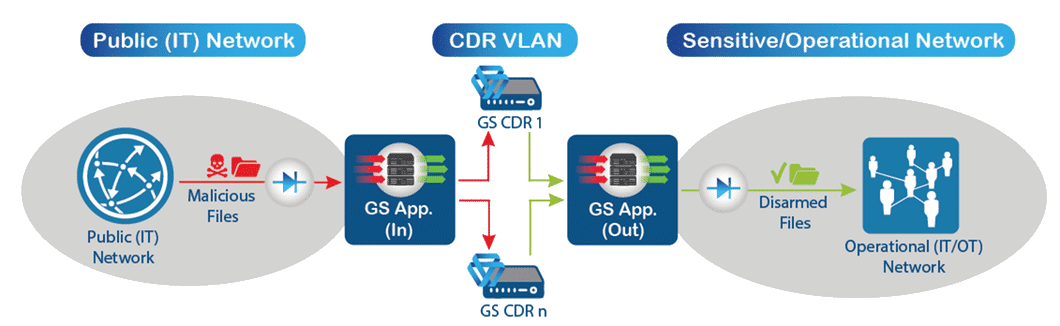
- Incident containment with network segmentation: Best-practices calls for a separation of IT and OT networks, with the realization that IT security incidents are often inevitable, but should be contained to prevent propagation leading to an enterprise-wide disruption impacting mission-critical network segments. GateScanner Multi-source and GateScanner Injector should be used to ensure uni-directional data transfer between networks, ensuring the one-way passage of safe files, preventing malicious files from being transferred in to OT/ICS networks.
Summary
The entire operational security and industrial eco-system are changing at a rapid pace. This heightens the risks these environments are facing today. Sasa Software with its GateScanner CDR technology is the only pure-play CDR vendor mentioned in Gartner’s OT security market guide. This technology could be utilized to mitigate several cyber risks and aid in several use cases, thus facilitating the adoption of new technologies in the OT environment while maintaining the highest levels of security.


