Tackling Qbot and preventing Ransomware Attacks
The infamous Qbot banking trojan has recently been spotted again, infecting tens of thousands of machines to date, mainly in the US
Also known as Quakbot, QakBot and Pinkslipbot, the Qbot trojan is a highly-maintained malware, with sophisticated evasion and persistence capabilities, and equipped with a worm-like functionality enabling it to spread quickly through networks.
Method of distribution
The malware is designed to steal domain and banking credentials and is usually hidden within a malicious document.
Arriving as an attachment to an email sent from a familiar address (usually hacked), it is disguised as an innocent-looking invoice, payment notice or other banking document.
When the user opens the document, he/she is prompted by a spoofed system or security message, to click a macro-enabling button such as ‘Content enable’ (see image below).
Once enabled, a script is activated prompting a chain of hidden processes that install multiple components of the malware at various locations on the victim’s machine.
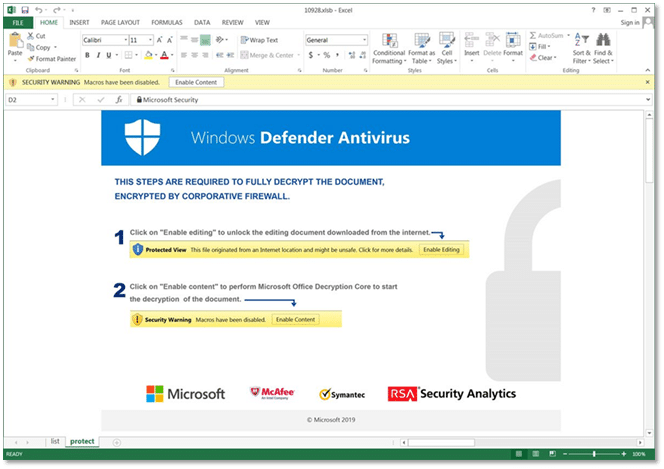
A spoofed Windows Defender message
Prevention strategy
To avoid being infected, users should be instructed never to enable content on incoming files.
On the backend, administrators would do well to install file-disarming tools on their email gateways. These are tools capable of stripping all incoming attachments of any embedded active codes. File disarming, also known as file sanitization, is the preferred solution for file-based cyber-threats since it eliminates the need to rely on user-adherence, and they completely bypass the risk of inevitable user error.
GateScanner® Mail Gateway from Sasa Software offers advanced email sanitization capabilities with extreme configuration options for any email system. Utilizing an award-winning, Content Disarm and Reconstruction (CDR) technology, Gatescanner Mail provides network administrators with complete control over the cleansing and disarming processes, down to a granular level. Incoming files are deconstructed to their basic components, cleansed from format-foreign contaminants, and scanned with multiple AV’s. Finally, the files are reconstituted to their original form, in strict adherence to their native formats, and content-identical – yet fully purged files – are produced and then safely and transparently inserted back into the email stream..
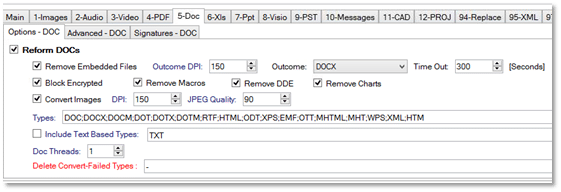
GateScanner Mail control panel: MS Word doc. CDR definitions
Conclusion
Applying a CDR-based network defense strategy on incoming file channels gives the IT security team the most advanced tools available to prevent and thwart file-based cyber-attacks such as the Qbot trojan, while maintaining minimal impact on the functionality and day to day operations of the organization.
Keyword: Sanitize email

